When you normally hear about a “hack”, or some “hackers” getting free services, stealing stuff or making their way through systems, the visual that comes to mind is a dude-in-a-hoodie leaning infront of a matrix-like screen, digging into crazy looking code. More often than not, it’s way simpler than that. Recently I’ve been testing covid payment systems for fun (yes, my fun is weird). The vulnerabilities come up too frequently, but they are quite simple, and can be found by anyone really. So simple that it begs the question of why were they not tested by the people that should be keeping our medical data safe.
In my first post on a similar issue I found an unprotected voucher system. This time around, it was the familiar price injection bug.
TL;DR
I thought finding one bug in one country’s border-covid-testing payment system is amusing and harmless. But now, flying to a different location, I came across another payment exploit. One that’s so bluntly left untested, the amusement left its place for worry.
Disclaimer
I did not actually use what I got and reported the bug.
I do not suggest people try to get free services through any kind of exploitation. This is meant to help secure those that are exposed.
My hope is that developers become more vigilant with systems, especially ones that deal and hold personal and medical information of literally everyone that crosses their country’s borders.
I do think, however, that testing, at home for these kinds of bugs is contributing to the greater good of the internet.
A non-technical rant
The airline I’m booked with had sent a rough scare-mail, warning that I should take multiple actions before arriving at the airport. Should I fail to complete one of them, the letter said, I’ll be denied from boarding the flight.
One of those steps was booking a pre-paid (no more “pay when you get there”) variant Covid test. If you live at the destined country you’re probably familiar with the requirement. A variant test has to be booked with one of the government approved providers. There are roughly fifty different ones, offering different levels of service in a range of prices. Like most customers, I filtered the list and sorted it by the cheapest test offered which was around $30. Not free, but still reasonable. The link led me from the government’s page to the provider’s, where a new price was shown: $95.99.
Now, I don’t like the idea of paying for a such a test, just 24 hours after taking another mandatory one. But when I’m asked to pay almost as much as the flight, tripling the price in a matter of seconds, it makes me uncomfortable, to say the least. While I’m aware of the risk, and am willing to take the necessary precautions, I am not enjoying playing a pawn in the recently-created market of testing providers.
With no illegal intentions, but definitely with a lets-see-if-I-can-catch-them-with-their-pants-down approach, I started booking a test.
Let the games begin
I started playing around. Looking for missing headers, places where I can fiddle with discount codes, or other features I can take advantage of, but found none. I reached the end of the process and the final screen where the system presented a large button saying “Pay now”.
Let’s look under the hood
I fired up Burp and made sure my requests are being proxied through. Then, I started forwarding irrelevant outgoing requests for metrics and inexplicable GET requests for strange metric services. Did I mention how enraging it is to learn the piles of crap we users send to an endless list of trackers in the internet?
And there it was, the request I was looking for:
POST /submit/<test ID number>
& ...body parameters...
& q271_price=95.99
Hello!
What do you mean the price is part of the parameters? Am I “being asked” to let the payment system know how much I want to pay?
Well how about 0.00?
Naively, I thought that simply “0” is an edgecase that might trigger a piece of input validation code (long story short, it ain’t). So I first checked “1.00” and “0.99”, all went with apparent issues.
And there it was, my new shopping cart summary:
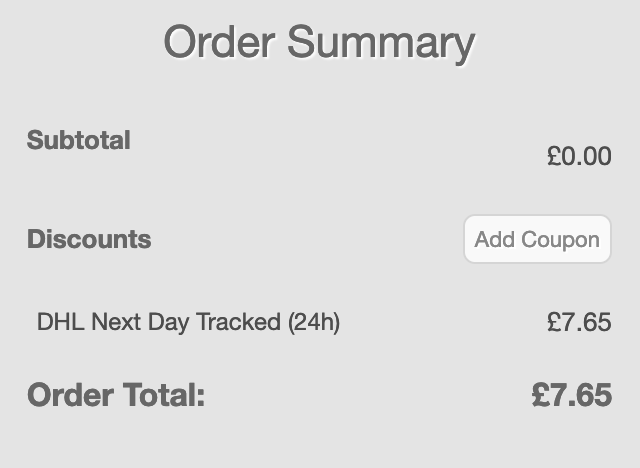
Yes, I was still asked to pay for shipping. I know, this is a robbery!
Heck, there’s still a coupon code option there. Am I pushing too far?
As always, moral of the story
Pretty straight forward by now innit?
A moment of seriousness though:
- Employ Zero trust. Incoming requsts should be authenticated for identification, and their parameters should be validated
- Having the above said, some parameters, should not be parameters! A price should be a result of backend computation, not something coming in as a request attribute. Having the browser dictate the price is letting the customer dictate the deal terms
- The fact that a UI shows certain details and hides others, does not make the system secure. This is just another form of security through obscurity
- Another form of obscurity was the list of some 100 different parameters sent in the request. While I’m not sure this was done intentionally (judging by the number of empty-value keys and their cryptic names I suspect it was), hiding the price is not a valid approach. It is searchable, and with the right tools it really can’t blend in the crowd
Another general financial note I have to make:
People are motivated by incentives. In the western capital environment we live in, more often than not, those incentives are financial. Any merchant on the surface of the internet is a target for schemers. Let alone one that’s getting rich on the backs of poor travellers, forced to pay for a service they don’t want.
Where am I going with this:
- Business owners: don’t take it too far. It’s okay to make money for a service. It can invite unwanted attention charging for a test kit and a lab result somewhere around 100X of the actual cost.
- People might get angry and actually use things like the described above for the benefit (and your loss)
- Protect yourself. Even in a shallow manner. Test the systems, validate inputs, pay for professional services and periodic reviews
- This was one out of fifty-something goverment approved service providers. If this is the security level of the first one chosen, what’s going on with the rest? What’s going on with the security of the customers? Their medical tests results?
Shortly after writing these lines, I found the next email waiting in my inbox:
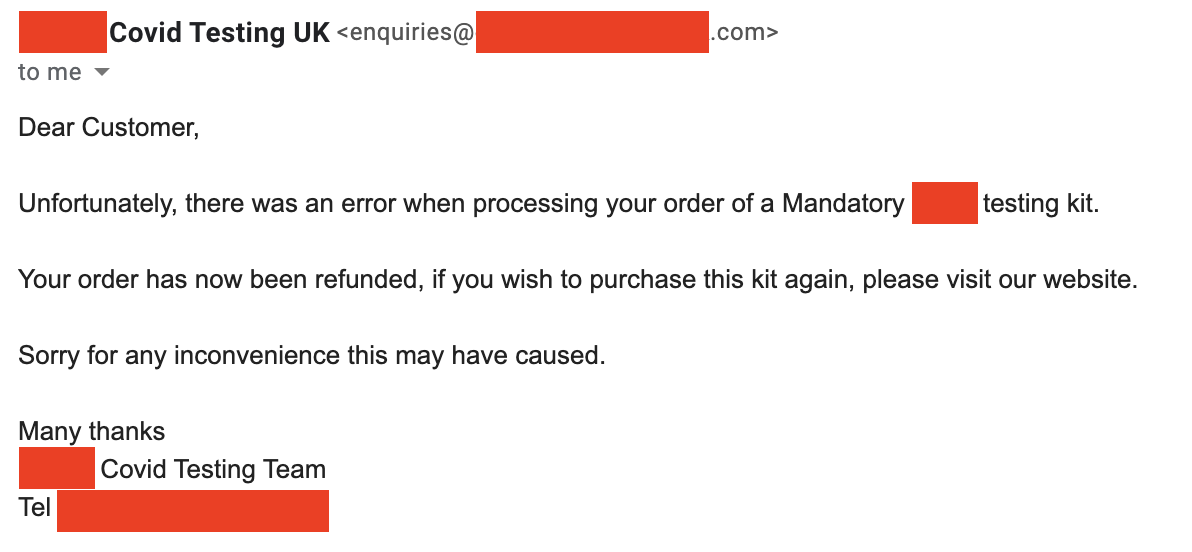
So, someone, I assume during a manual checkup, noticed the anomaly and took care of it. However, you’d be interested hear that the bug is still there 🤷.
On to the next provider then…
Thank you for reading 🖤
Feel free to reach out with questions or comments.


